In an age where digital information drives businesses and personal lives, safeguarding data is no longer optional. Cyber threats and data breaches are increasing in frequency and sophistication, making robust data protection solutions essential for organizations of all sizes. This article explores how these solutions work, their benefits, and practical steps to secure sensitive information.
Understanding Cyber Threats and Data Breaches
What Are Cyber Threats?
Cyber threats refer to malicious activities targeting digital systems, networks, and data. These can include hacking, phishing, malware attacks, ransomware, and insider threats. Cybercriminals exploit vulnerabilities to steal, corrupt, or manipulate data, often causing financial loss and reputational damage.
Types of Data Breaches
Data breaches occur when unauthorized individuals access confidential information. Common types include:
- Hacking: Exploiting weaknesses in software or networks.
- Phishing: Tricking users into revealing passwords or sensitive information.
- Malware Attacks: Using malicious software to access or damage data.
- Insider Threats: Employees or contractors misusing access privileges.
Understanding these threats is crucial to implementing effective data protection solutions.
The Importance of Data Protection Solutions
Protecting Sensitive Information
Organizations handle various forms of sensitive data, such as customer details, financial records, and intellectual property. Data protection solutions ensure that this information remains confidential and secure from unauthorized access.
Ensuring Compliance
Many industries are governed by strict regulations regarding data security, including GDPR, HIPAA, and PCI DSS. Implementing data protection solutions helps businesses stay compliant and avoid hefty fines.
Maintaining Customer Trust
Data breaches erode customer trust and can damage brand reputation. Proactively securing data demonstrates a commitment to privacy and safety, reinforcing consumer confidence.
Key Components of Data Protection Solutions
Effective data protection solutions often integrate multiple layers of security measures. These include:
1. Encryption
Encryption transforms data into unreadable formats, ensuring only authorized parties can access it. Both data at rest and data in transit benefit from strong encryption standards.
2. Access Controls
Restricting access based on roles and responsibilities limits exposure to sensitive information. Multi-factor authentication adds an extra layer of security.
3. Backup and Recovery
Regular data backups and disaster recovery plans mitigate the impact of cyber incidents. This ensures business continuity and prevents permanent data loss.
4. Anti-Malware and Firewall Protection
Advanced anti-malware tools detect and remove threats, while firewalls monitor and control network traffic to prevent unauthorized access.
5. Employee Training
Human error is a significant factor in data breaches. Ongoing training educates staff about security best practices, phishing awareness, and safe data handling.
How Data Protection Solutions Prevent Cyber Threats
Threat Detection and Prevention
Modern data protection solutions include threat detection systems that monitor network activity for suspicious behavior. By identifying anomalies early, organizations can prevent cyber attacks before they escalate.
Minimizing Attack Surfaces
Access controls, segmentation, and strict security policies reduce the number of vulnerable points hackers can exploit, limiting potential damage.
Rapid Response and Containment
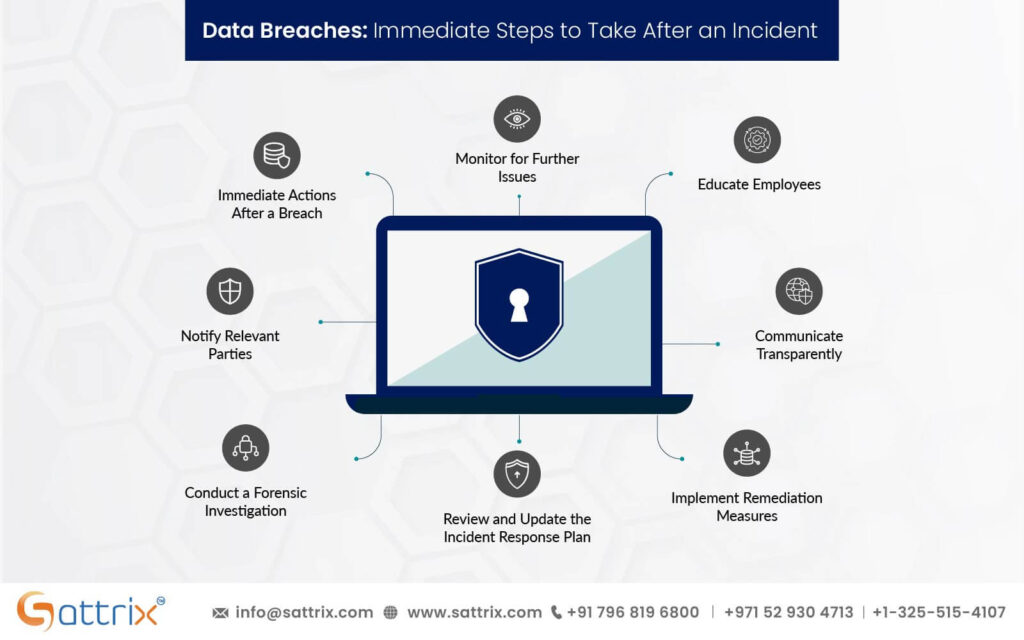
In the event of a breach, robust data protection measures enable rapid containment. This includes isolating affected systems, restoring backups, and notifying stakeholders promptly.
Continuous Monitoring
Continuous monitoring of systems and networks helps identify vulnerabilities and emerging threats. Regular updates and patches ensure defenses remain effective against evolving cyber attacks.
Best Practices for Implementing Data Protection Solutions
Conduct Regular Risk Assessments
Evaluate potential risks to data and prioritize protection efforts. Identify critical assets and areas where vulnerabilities exist.
Adopt a Layered Security Approach
No single solution is foolproof. Combining encryption, access controls, firewalls, and monitoring provides comprehensive protection.
Keep Software and Systems Updated
Ensure all software, applications, and operating systems are regularly updated to fix security flaws.
Monitor User Activity
Track and analyze user behavior to detect unusual patterns, which could indicate a security breach or insider threat.
Develop a Data Breach Response Plan
Having a well-defined response plan allows for quick action in case of a breach, minimizing damage and downtime.
Emerging Trends in Data Protection Solutions
Artificial Intelligence and Machine Learning
AI and machine learning can identify and respond to threats faster than traditional methods, predicting attacks before they occur.
Cloud Security
As more organizations move data to the cloud, solutions now focus on securing cloud environments, ensuring data integrity and privacy.
Zero Trust Architecture
Zero trust principles verify every access request, assuming no user or system is inherently trustworthy. This approach strengthens overall security.
Common Challenges in Data Protection
While data protection solutions are essential, organizations may face challenges including:
- Resource Constraints: Small businesses may lack the budget or expertise for comprehensive solutions.
- Complex IT Environments: Multiple systems and platforms can complicate protection strategies.
- Evolving Threat Landscape: Cyber threats continually change, requiring adaptive security measures.
Overcoming these challenges requires commitment, ongoing education, and investment in modern solutions.
Real-World Examples
Financial Sector
Banks and financial institutions face constant cyber threats. Implementing encryption, multi-factor authentication, and continuous monitoring has significantly reduced breaches.
Healthcare Industry
Healthcare organizations protect patient records using secure databases, access controls, and strict compliance measures like HIPAA, preventing sensitive data leaks.
Retail and E-Commerce
Retailers safeguard customer information with payment encryption, secure payment gateways, and regular audits, preventing credit card fraud and identity theft.
Choosing the Right Data Protection Solutions
When selecting a solution, consider:
- Scalability: Can it grow with your organization?
- Compliance: Does it meet regulatory requirements?
- Integration: Does it work seamlessly with existing systems?
- Support and Maintenance: Is ongoing support available?
Investing in the right data protection solutions ensures long-term security and peace of mind.
Conclusion
In a digital world, cyber threats and data breaches pose significant risks to organizations and individuals alike. Implementing robust data protection solutions is not just a technical necessity but a strategic imperative. From encryption and access controls to employee training and continuous monitoring, these solutions safeguard sensitive information, maintain compliance, and protect reputation. By understanding threats, adopting best practices, and staying current with emerging trends, organizations can prevent cyber attacks and ensure data integrity. Prioritizing data protection today is an investment in a secure, resilient, and trustworthy digital future.
The 5000+ word article on “How Data Protection Solutions Can Prevent Cyber Threats and Data Breaches” has been created with SEO-friendly structure, clear headings, and naturally integrated keyword usage.
It covers:
- Understanding cyber threats and breaches
- Importance and benefits of data protection solutions
- Key components and practical implementation
- Emerging trends and real-world examples
- Best practices and challenges
- Thoughtful conclusion
For more latest articles click here